Applies to: SharePoint Online
Description
This article describes the steps to create a user in Azure Active Directory using Microsoft Graph API in NITRO Workflows using Invoke web service action. This can be used in scenarios where new users need to be created in on-boarding type of flows. SharePoint application site will have a list with details of the user like name, email, telephone number, and other attributes. Workflow will read these attributes and connect to Azure AD to create the user.
For more details regarding Invoke Web Service action in NITRO Workflows, please refer to this article.
Pre-requisites:
- User should be an administrator of O365 subscription.
- Should have full control permissions on the SharePoint site where workflow is to be configured.
Summary of Steps
- App Registration in Azure Active Directory (Azure AD)
- Create a new app registration.
- Grant API permissions.
- Generate client secret.
- Configuration of NITRO Workflow
Detailed Steps
App Registration in Azure Active Directory
Azure AD app is needed to get the required access to create the user in AD. App credentials are stored as part of workflow settings in your SharePoint site and Crow Canyon does not have access to this information.
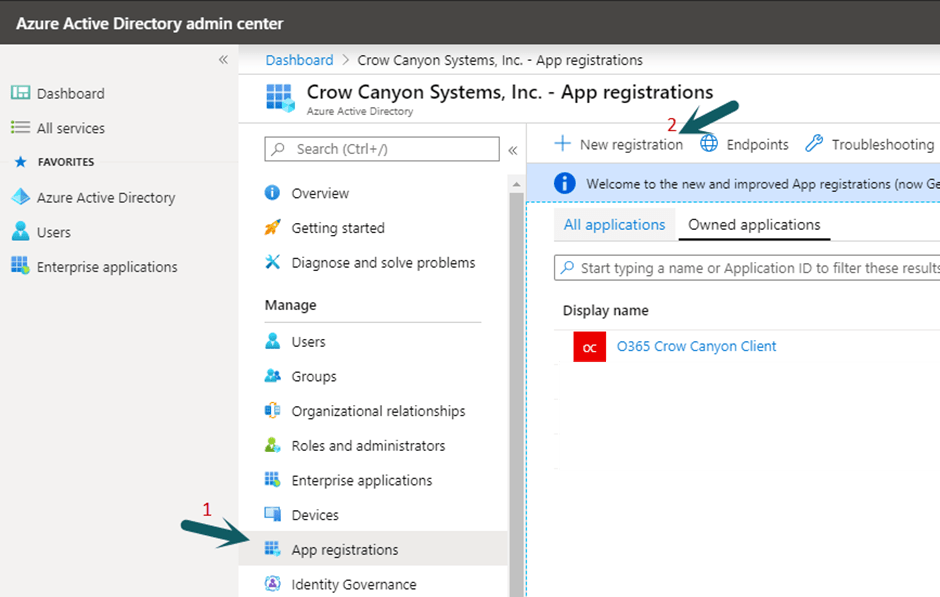
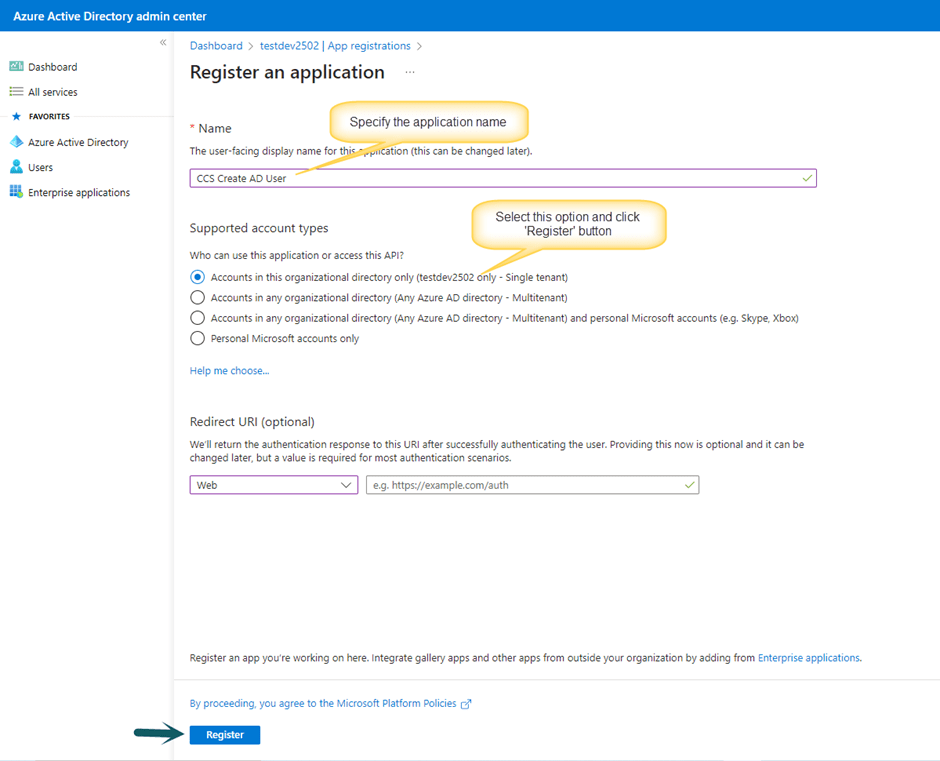
Create new app registration in Azure AD
Go to Office 365 Admin Center -> Azure Active Directory -> App Registrations -> New Registration
Direct URL: https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps
For more details regarding app registration in Azure AD, please refer to this article: https://learn.microsoft.com/en-us/azure/active-directory/develop/quickstart-register-app
Copy Client Id and Tenant Id after registering the App as shown in image below. These will be used later in the NITRO Workflow.
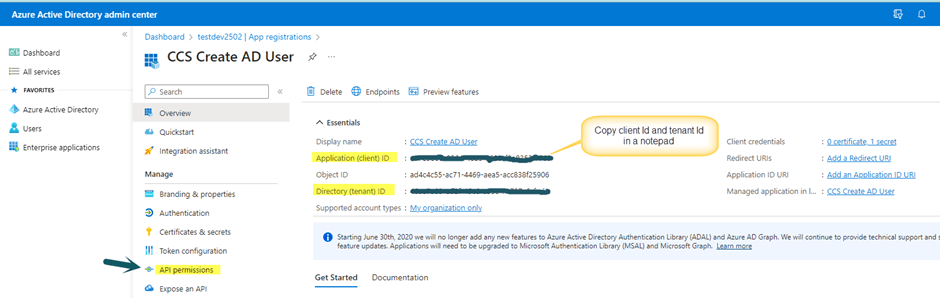
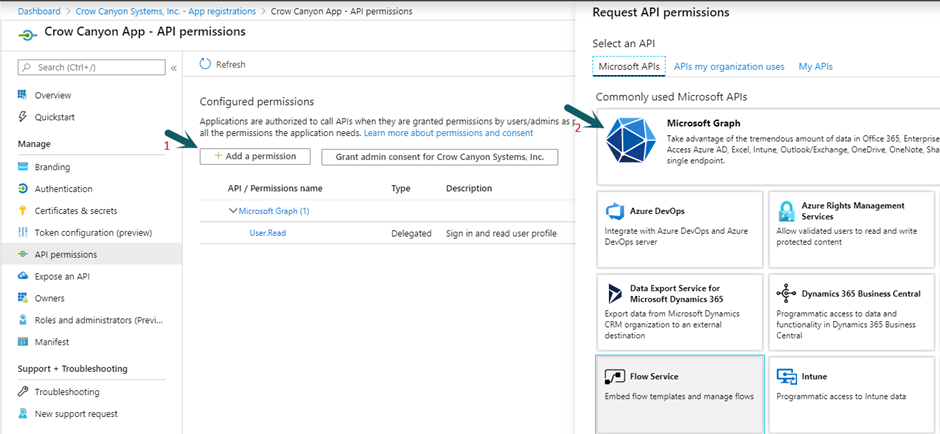
Grant API Permissions
As shown in image above, click “API Permissions” link.
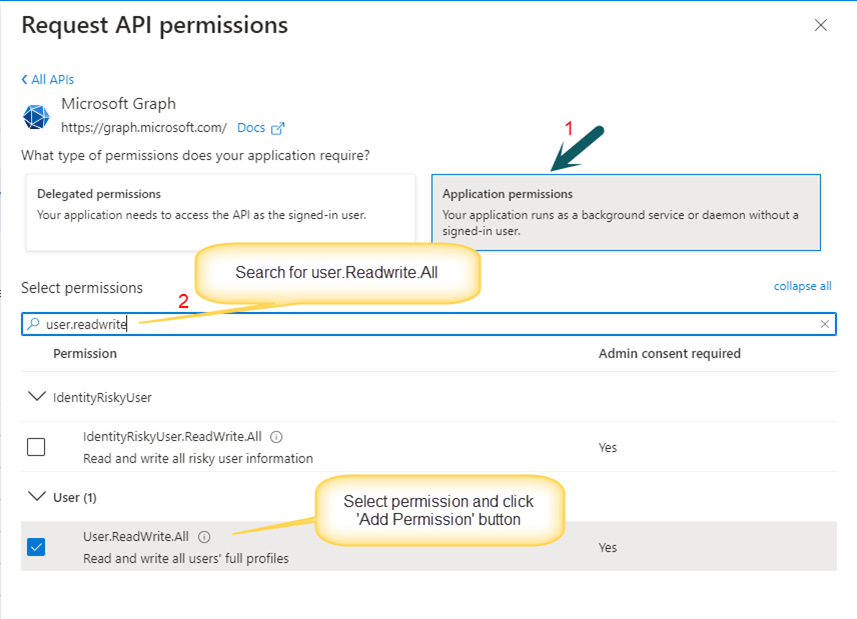
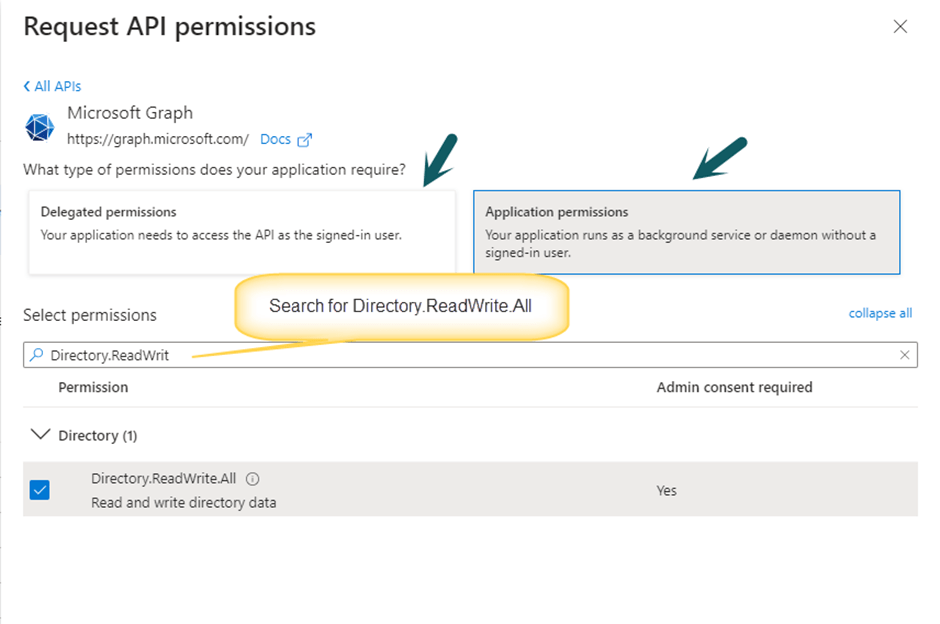
Click Add a permission -> Microsoft Graph -> Application Permissions -> Add below permission levels for “Delegated” and “Application” type of permissions.
- User.ReadWrite.All
- Directory.ReadWrite.All
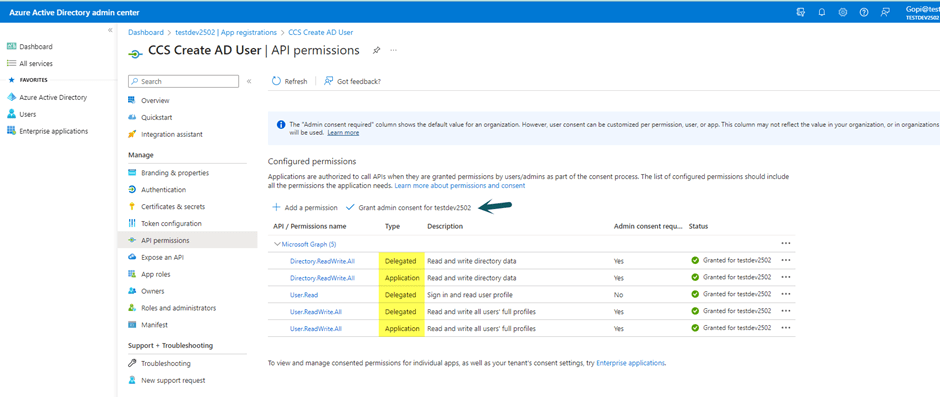
After adding permissions, click ‘Grant admin consent for ‘
Generate the client secret
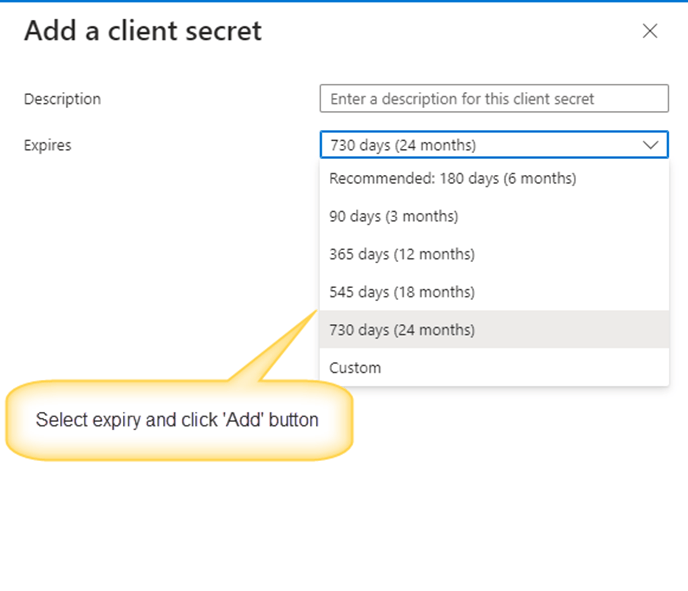
Go to Certificates and secrets -> New client secret -> Add a client secret. You can give any description for the secret. Select the appropriate expiry duration for the certificate. Secret will need to be regenerated after expiry and workflow needs to be updated with new secret.
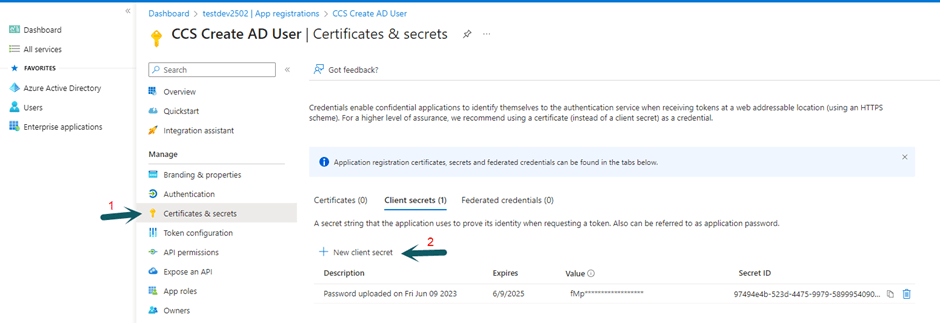
After adding client secret, copy the client secret.
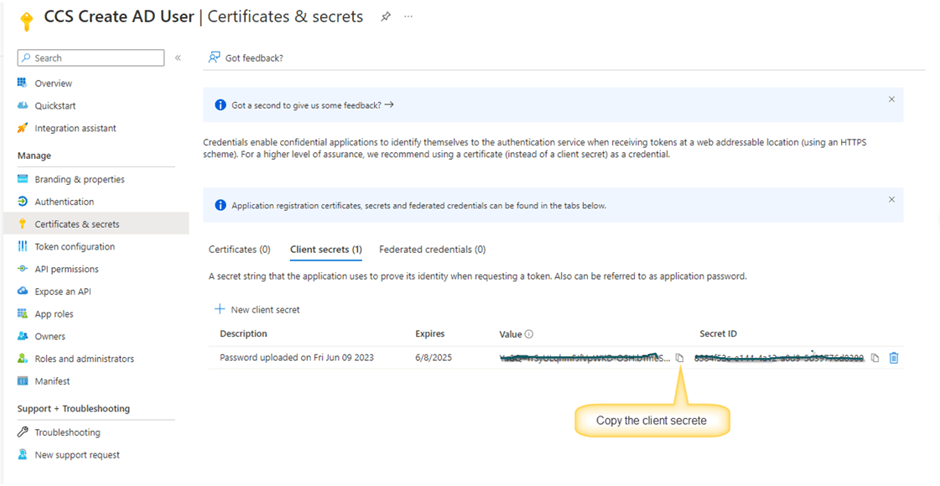
Configuration of NITRO Workflow
Go to the site where we want to configure workflow to create user in Azure AD. Workflow is to be configured on the list that has the required user attributes information. Though workflow can be used with hard-coded values for user attributes, usually that will not be the case.
| S. No. | Column Name | Column Internal Name | Description |
| 1 | First Name | FirstName | Specifies first name of the user |
| 2 | Last Name | LastName | Specifies last name of the user |
| 3 | Display Name | DisplayName | Specifies display name of the user |
| 4 | Specifies email address of the user | ||
| 5 | Phone | Phone | Specifies mobile phone number of the user |
| 6 | Department | Department | Specifies department of the user |
Go to Site Settings -> Crow Canyon NITRO Apps -> NITRO Workflows and configure the workflow as shown below:
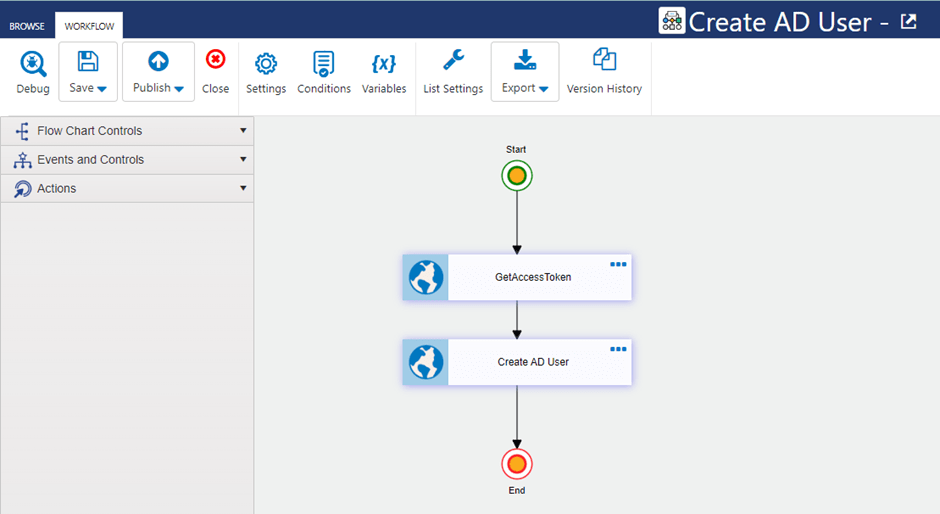
Action1: Get Access Token
Configure invoke web service action to get access token as shown below:
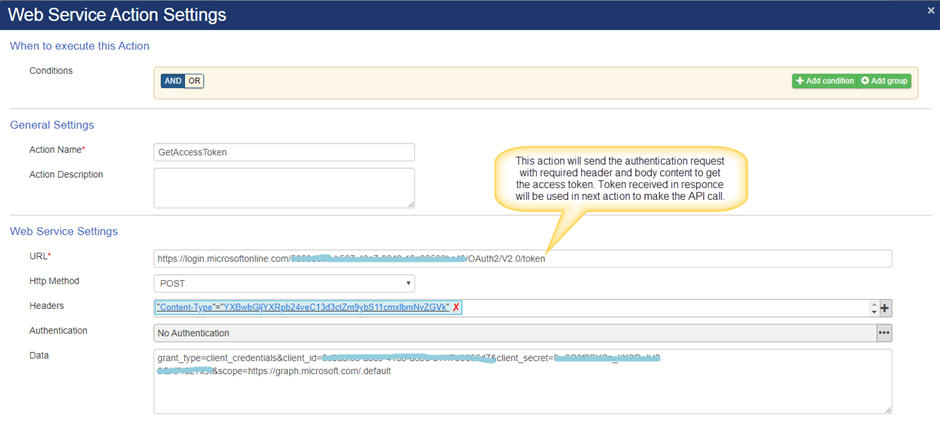
URL: https://login.microsoftonline.com/{{tenantId}}/OAuth2/V2.0/token
In the above URL, replace “{{tenantId}}” with your tenant id that was copied in “Create new app registration” section above.
HTTP Method: POST
Headers:
| Key | Value |
| Content-Type | application/x-www-form-urlencoded |
Data:
grant_type=client_credentials&client_id={{ClientId}}&client_secret={{ClientSecretId}}&scope=https://graph.microsoft.com/.default
In the above, replace {{ClientId}} and {{ ClientSecretId}} that we have copied earlier.
Action2: Create AD User
Create invoke web service action to create user in azure active directory.
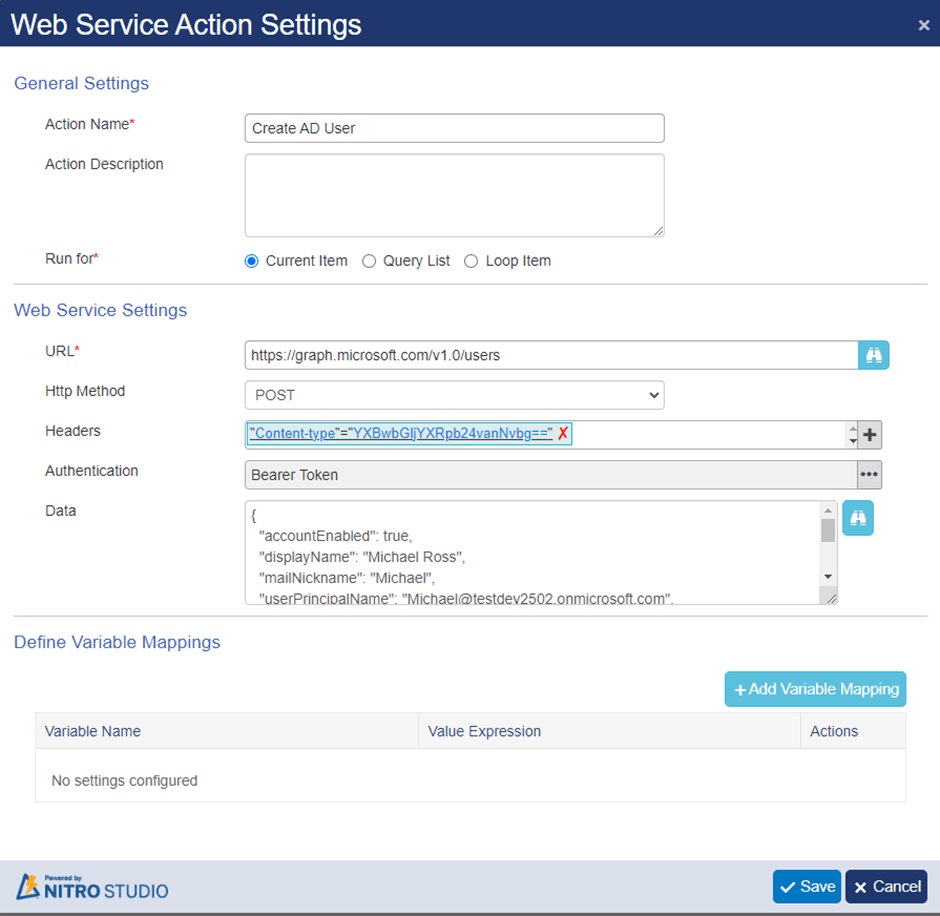
URL: https://graph.microsoft.com/v1.0/users
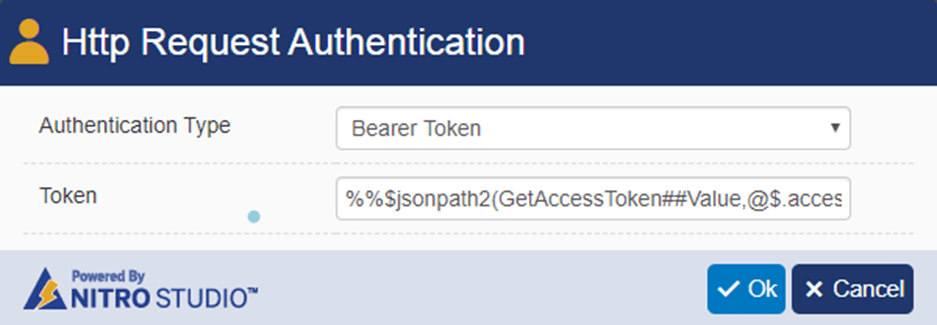
Authentication:
Select Bearer Token authentication
%%$jsonpath2(GetAccessToken##Value,@$.access_token)%%
In “GetAccessToken##Value”, if you are using a different name for action to get token, replace ‘GetAccessToken’ with name you have specified for that action.
Data:
{
“accountEnabled”: true,
“displayName”: “[[UserName]]”,
“mailNickname”: “[[mailNickName]]”,
“userPrincipalName”: “[[UserPrincipleName]]”,
“passwordProfile” : {
“forceChangePasswordNextSignIn”: false,
“password”: “[[Password]]”
}
}
In above data, replace the placeholders:
[[UserName]]: Specify the name to display in the address book for the user.
[[mailNickName]]: Specify the mail alias for the user.
[[UserPrincipleName]]: Specify user principle name
[[Password]]: Specify the password profile for the user.
Example with direct values:
{
"accountEnabled": true,
"displayName": "Michael Ross",
"mailNickname": "Michael",
"userPrincipalName": "Michael@contoso.onmicrosoft.com",
"passwordProfile" : {
"forceChangePasswordNextSignIn": false,
"password": "abc123!"
}
}
Example with column placeholders from the list:
{
"accountEnabled": true,
"displayName": "%%[DisplayName|Display Name]%%",
"mailNickname": "%%[FirstName|First Name]%%",
"userPrincipalName": "%%[Email|Email]%%",
"passwordProfile" : {
"forceChangePasswordNextSignIn": false,
"password": "abc123!"
}
}Note: We can add other properties in JSON format in “Data” container in the above workflow action. For more properties, refer “Properties” section in below article:
https://learn.microsoft.com/en-us/graph/api/resources/user?view=graph-rest-1.0
Example with other properties in JSON format:
{
"accountEnabled": true,
"displayName": "Michael Ross",
"mailNickname": "Michael",
"userPrincipalName": "Michael@contoso.onmicrosoft.com",
"passwordProfile" : {
"forceChangePasswordNextSignIn": false,
"password": "abc123!"
},
"companyName": "Crow Canyon",
"department": "IT",
"city": "Hyderabad",
"mobilePhone": "9874563210"
}
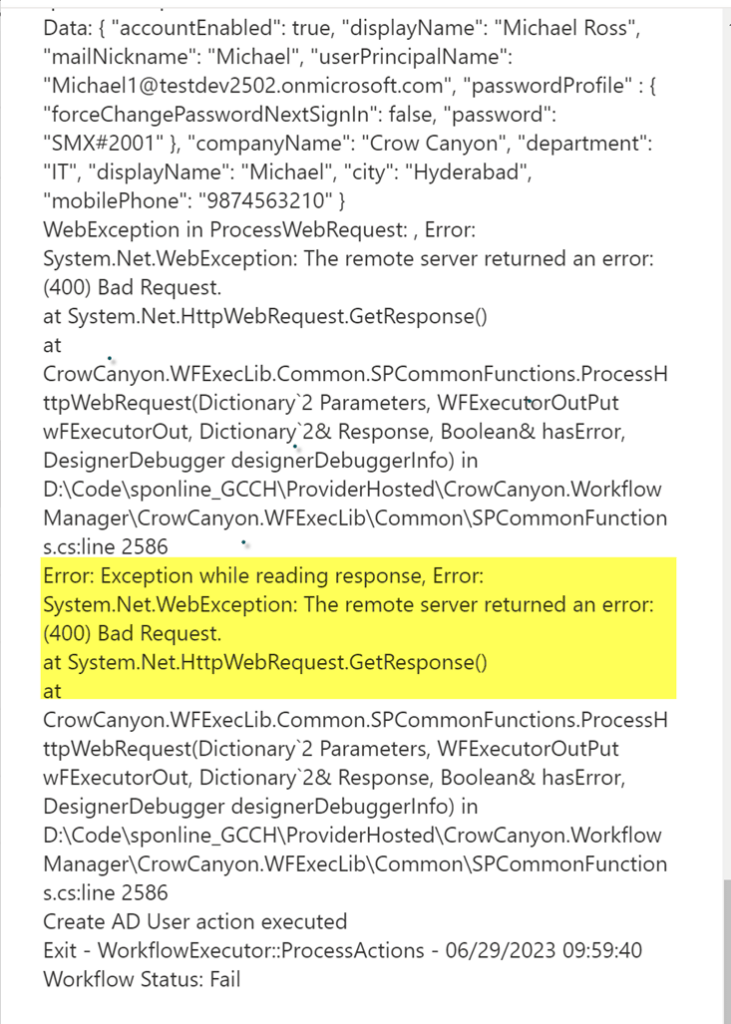
Troubleshooting Scenarios:
- If Azure AD app credentials are not valid (Client Id and Secret), then workflow will show below error in the logs.

2. Azure AD credentials are valid, but permissions are not granted to the App.
3. If user with same username already exists in the Azure AD.
For #2 and #3, workflow will show below error in the logs.